The matrix below details the areas in cybersecurity where power companies should be focusing their time and resources. We suggest that power companies invest in technologies that are shaded in green, explore the prospect of investing in technologies shaded in yellow, and ignore areas shaded in red.
Due to the importance of cybersecurity for a company in the power sector, and the fact that just one attack can bring down an entire power network and have severe cross-sector implications, companies should virtually invest across the entire cybersecurity value chain. Different types of cyberattacks focus on different sections of the value chain. For example, email security is important for preventing phishing attacks, whereas threat detection and response, which may likely include endpoint detection and response, would be useful for finding and countering malware or zero-day threats.
Cybersecurity has never been more important to the power sector. A joint study from the World Government Summit and EY found that the number of cyberattacks on energy companies in the US and Canada increased by 71% between 2021 and 2022, with critical infrastructure assets representing the main targets for cybercriminals. This means that power companies must start taking cybersecurity more seriously and invest throughout the value chain to cover all eventualities.
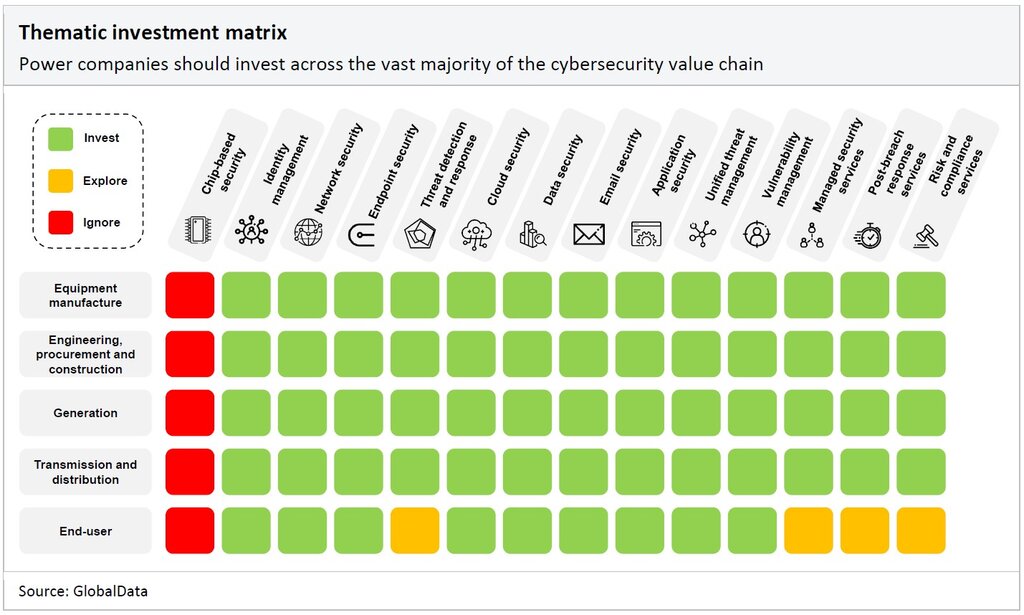
As the graphic shows, power companies should not focus on chip-based security. This is because of the advanced and capital-intensive nature of semiconductor manufacturing. Investing in chip fabrication and foundry to ensure chip-based security would be a misguided investment given the number of trusted leading cybersecurity vendors, thus, the secure chips are sourced from these leading vendors.
Furthermore, the end-user or consumer is not always in the position to invest in cybersecurity services, such as managed security services, post-breach response services, or threat detection and response. Nevertheless, end-users should take all necessary steps to keep themselves cyber-safe at home with effective management of their passwords. Notably, with the proliferation of smart meters around the world, especially in advanced economies in Europe, the companies providing smart meter services should also ensure strong cybersecurity for their product, which may constitute an entry point for hackers. Smart meter installations in the UK increased almost fivefold to 25.7 million between 2017 and 2022, according to the Department for Business, Energy and Industrial Strategy. If access is gained to the meter, a hacker could take control of the energy usage of the property, leading to higher energy bills and potentially even a complete blackout.
How digitalization and the energy transition accelerate the need for cybersecurity
One of the lasting changes resulting from the COVID-19 pandemic was the immediate switch to home working, which has now resulted in many companies adopting a hybrid or fully remote working policy. Companies were forced to speed up their journey to digitalization, and this sudden increase in demand for digital devices (mainly laptops and tablets) increased the cyber threat worldwide. Digitalization has increased and becomes more decentralized as workers are working from home more often. This is a cybersecurity challenge because using a laptop or personal device to access company data leads to greater exposure to cyberattacks, according to the UK National Cyber Security Center. This is because employees are less likely to run cybersecurity scans and homeworkers use Wi-Fi that is more susceptible to cyberattacks and does not have prevention and detection measures. The energy sector, however, due to its greater number of manual workers, has a smaller proportion of homeworkers than other sectors which are IT or service-based.
In terms of adhering to net-zero commitments while delivering more power to a greater number of people, countries and companies worldwide must deploy greater digitalization, including the use of smart grids aimed at improving the efficiency of the electric grid. Smart grids differ from the traditional grid because information communication is two-way; consequently, securing the (often sensitive) information is more difficult and thus they are more exposed to cyberattacks. Smart grids are vulnerable to phishing, denial-of-service, malware spreading, eavesdropping, and traffic analysis, with denial-of-service attacks being the most potentially damaging and frequent. Digitalization, as mentioned, increases the risk of cybersecurity, and thus, any potential increase in deployment of digitalization must be met with a commensurate increase in cybersecurity capabilities.
Another way in which the electric grid is undergoing a transition is through the integration of an increasing number of distributed energy resources (DERs). Some of these come in the form of renewable energy sources, such as solar photovoltaic (PV) units and wind-generating units, and many of these lie at the grid edge. DERs such as solar PV units create an expanded attack surface for hackers to exploit, and the management and operation of these assets create a greater need for automation. This introduces information exchanges between the DER and a utility’s distribution control system, and the Industrial Internet of Things (IIoT) technologies that enable these exchanges can sometimes lack communications security. Therefore, the need for adequate cybersecurity protection of these assets becomes clear.
How geopolitics accelerates the need for cybersecurity
The last few years have seen an increase in tensions around the world, especially between major powers. The Russian invasion of Ukraine has had several geopolitical reverberations, one of which is that businesses are taking cybersecurity more seriously. Due to the strategic importance of the power sector, and the fact that it essentially underpins every other sector, geopolitically motivated cyberattacks are very common. Furthermore, one side-effect of the war in Ukraine has been its impact on global energy prices and supply, as European nations have sought to reduce their dependence on gas imported from Russia. With greater concerns around energy security, the importance of preventing any cyber-related disruption could not be clearer.
The Russia-Ukraine conflict is the most pertinent example of geopolitics influencing cyberattacks. Russia’s alleged cyber military group ‘Sandworm’ is believed to be responsible for the 2015 attack on Ukraine’s power grid, the 2017 NotPetya global attacks, and a foiled two-wave attack in April 2022 on Ukraine’s high-voltage electricity substations aiming to shut off electricity for two million Ukrainians. If the attack was successful, it would have been the largest attack since the invasion began in February 2022. These attacks are certainly not limited to Ukraine either. In Europe, German wind energy companies Nordex, Enercon, and Deutsche Windtechnik have been targeted by cyberattacks since the invasion of Ukraine, while 22 energy companies in Denmark suffered attacks in May 2023 which forced them to disable their internet connections. Although impossible to prove, it is both likely and logical that these attacks are geopolitically motivated. Since Russia invaded Ukraine, European countries have recognized their dependence on Russian oil and gas as a geopolitical weakness, and many have pledged to wean themselves off Russian hydrocarbons. To achieve this, promoting renewable energies such as wind power can be seen as a longer-term replacement, which could increase European energy diversification and reduce dependence on Russia. In the case of the March 31, 2022, attack on Nordex, pro-Russian ransomware group Conti claimed responsibility.
The need for cybersecurity is self-evident for power companies, which are innately tied to the functioning of a country’s economy. The Russian invasion of Ukraine has seen the threat of such attacks on the sector increase. Utilities should be most alert to the heightened risk of cyberattacks because of the geopolitical situation playing out between Europe and Russia over energy. Power companies in countries that are supporting Ukraine, such as the UK, are also at risk of proxy attacks on their infrastructure assets.
How ESG accelerates the need for cybersecurity
One of the core fundamentals of ESG is achieving good governance. To ensure this is met, companies must comply with appropriate cybersecurity legislation. As cybersecurity has risen up the board agenda of companies and businesses worldwide, regulators have taken notice. ‘The Impact of Cybersecurity’ section has previously noted the critical nature of the power sector and the role it plays in domestic and regional economies. Consumers can be targeted not just through the theft of personal information and data, but also through the disruption of services, such as electricity or gas. The EU has noted that, due to the digitized energy system across the bloc, an attack on one nation-state can cause a ripple effect on the energy systems of other countries.
As such, the EU has adopted cross-sector legislation that includes the NIS Directive (2016) and the Cybersecurity Act (2019). The former ensures that electricity suppliers and transmission and distribution operators must conform to cybersecurity requirements and notifications, with an obligation to respect minimum standards around risk mitigation minimization. The European Union Agency for Cybersecurity (ENISA, formerly the European Network Information Security Agency), which advises on cybersecurity matters, has produced guidelines and recommendations for energy companies about cybersecurity, including for smart grid, information sharing, and attacks against time-sensitive services. The Cybersecurity Act (2019) strengthens the powers of ENISA.
The NIS Directive was transposed into UK law in 2018, renamed the NIS Regulations. The NIS Regulations impose a host of new responsibilities on electricity and gas suppliers, which were updated in April 2022, and mostly focused on the management of cybersecurity risk and reporting of cyberattacks. The UK’s energy regulator Ofgem mandates the National Cyber Security Centre’s Cyber Assessment Framework, meaning that power companies can be fined or have their licenses revoked if they fail to manage their cyber risk appropriately or prevent or mitigate cyberattacks.
In the US, the Office for Cybersecurity Energy Security and Energy Response (CESER) has a strong focus on improving preparedness and mitigation of cyberattacks. The US Department of Energy has a Cybersecurity Risk Information Sharing Program that is a public-private initiative aiming to enhance the ability of the energy sector to identify threats using advanced sensors and the sharing of information between the state, companies, and third parties. Moreover, CESER and industry partners have developed the Cybersecurity Capability Maturity Model (C2M2), which aims at cybersecurity capability evaluation for private sector companies. The North American Electric Reliability Corporation (NERC) released standards for Critical Infrastructure Protection (CIP) in 2007, which include large fines for non-compliance—the largest being a $10 million fine imposed in 2019 on an organization that suffered 127 separate violations. The latest NERC CIP standards address supply chain risk, electronic security parameters, configuration change management, vulnerability assessments, as well as incident reporting and response planning.
Furthermore, successful cyberattacks have a significant ability to cause environmental damage. This often comes as a result of an attack on critical equipment and warning systems and can lead to gas leaks, oil spills, or other forms of pollution. Utility companies typically use supervisory control and data acquisition (SCADA) software for controlling their industrial assets, allowing the companies to collect data and control equipment in remote locations. SCADA systems are connected to the internet and thus vulnerable to cyber attackers. These attacks are common; for example, the aforementioned 2015 and 2017 attacks on the Ukrainian power grid as well as the infamous Stuxnet attack, whereby Iran’s nuclear power plants were significantly damaged, used this form of attack.
How a shortage of skills accelerates the need for cybersecurity
The decline in the pool of available talent in the energy sector as a generation of skilled workers begins to retire presents challenges in terms of cybersecurity. Firstly, the sector-wide shortage of workers is coupled with a lack of skilled cybersecurity professionals globally – an analysis by Fortinet, a cybersecurity vendor, states that there were 3.4 million unfilled cybersecurity jobs across the global industry as a whole in September 2023. Data from the International Energy Agency also shows that demand for cybersecurity professionals from utility companies surges significantly in the wake of a cyberattack. While this suggests a lack of long-term cybersecurity strategy on the part of companies, it may also indicate that the reason for low numbers of cybersecurity job postings in the sector in the buildup to an attack is due to a lack of available talent.
Furthermore, this shrinking of the workforce coupled with an increase in renewable energy assets located at the grid edge furthers the need for increased automation. With less manpower available, power companies can reduce costs and manual workload by digitizing and automating manual tasks, improving efficiency. However, as mentioned, automation brings about information exchanges on a network, creating a larger attack surface for hackers and providing them with many more entry points to an energy company’s systems.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.